Leveraging data analysis tools for IT rollouts in DBT

...or we weren’t sure whether their laptop needed to be replaced. Things which we couldn’t fix using code, we needed users to tell us. This meant that we couldn’t simply...

...or we weren’t sure whether their laptop needed to be replaced. Things which we couldn’t fix using code, we needed users to tell us. This meant that we couldn’t simply...

...from an interface that uses well-established, accessible Government Digital Services (GDS) design patterns. Where necessary the team have developed additional components to the same standards, backed by a holistic design...

...provide a range of services to help inspire, plan and learn about exporting, from identifying new markets to strategic planning. Sign up for our Learn to Export service on great.gov.uk...
...Service. I spent most of my time helping stakeholders design their content, making it simpler to understand and quicker to read. Often our experts do not even realise that they...
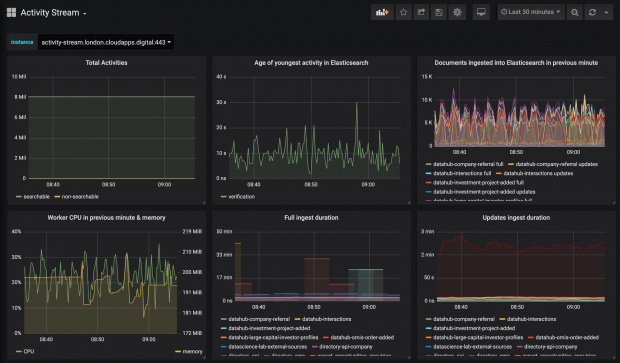
...breaks certain rules of API design. This is because many services hide their inner workings and present a different query language to the one used internally. This choice means that...

...give the user a better signposting experience. If users have a clear direction of where to go next, then we improve our chances of a website objective being achieved. It’s...

...working world. One way I have managed those specific times that I need my kids to pause before waltzing in is by creating a door sign. I have had mine...

...to senior stakeholders (such as under-resourcing). This enables timely course correction before code is built, and change becomes more complex. We also offer pragmatic solutions such as regular assurance reviews....

...or concept that I do not understand. What is code? Where is the cloud? One of the best bits about this DDaT team is there is never any shame in...

...from unstructured data, or even write code. Government departments routinely handle confidential and personal data. Therefore, using public AI tools that transmit data externally can post significant security and privacy...